Intel-based personal computers come with an Intel Management Engine (ME) built inside them. A brief introduction, from Wikipedia, for those new to this technology:
The Intel Management Engine (ME), also known as the Manageability Engine, is an autonomous subsystem that has been incorporated in virtually all of Intel's processor chipsets since 2008. The subsystem primarily consists of proprietary firmware running on a separate microprocessor that performs tasks during boot-up, while the computer is running, and while it is asleep. As long as the chipset or SoC is connected to current (via battery or power supply), it continues to run even when the system is turned off. Intel claims the ME is required to provide full performance. Its exact workings are largely undocumented and its code is obfuscated using confidential Huffman tables stored directly in hardware, so the firmware does not contain the information necessary to decode its contents.
The ME firmware interacts closely with BIOS firmware, and is often bundled with BIOS in one unified update package. The combination of: 1) the ME’s power, 2) the ME’s undocumented-ness, and 3) recent ME vulnerabilities (see here and here) have made the ME a recent topic of conversation for security researchers.
One firmware researcher is Plato Mavropoulos, co-maintainer of the Win-Raid site and the ME Analyzer tool. ME Analyzer is a great tool for inspecting ME firmware, many versions of which are archived on the Win-Raid site. (note: this archive includes only firmware images released publicly by computer manufacturers—this is not a bootleg site, or a site that would in any way violate an NDA)
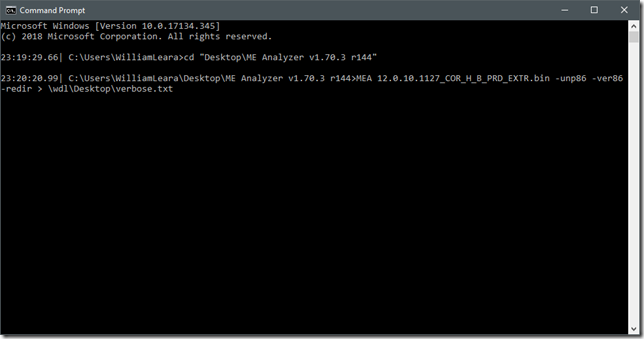
ME Analyzer is written in Python, and so can run on any OS that has Python v3.6 support. (i.e. pretty much all of them) The program is contained in only three files: MEA.exe, MEA.dat, and Huffman,dat. You can drag and drop an ME .bin image on top of MEA.EXE to open it up, but I found it best to run it from a command-line. Example:
Some notes on the command line syntax:
- The file I am analyzing is 12.0.10.1127_COR_H_B_PRD_EXTR.bin
- -unp86 unpacks the ME firmware
- -ver86 enables verbose mode unpacking
- -redir redirects the console output to a file
You can see the complete list of options by running MEA.EXE and typing –?.
ME Analyzer unpacks the .bin file into all the various partitions and modules that make up the firmware image. Here’s a snippet of a directory tree to show you what this looks like:
I’ve archived the full output of the tool; it’s over 7800 lines of text, so it’s pretty involved, but you can see the construction of ME firmware by taking a look here.
Conclusion
In conclusion, ME Analyzer is a great tool for PC/BIOS/firmware/ME hobbyists and researchers. If you are a security researcher or someone working intimately with the ME, then this tool should definitely be part of your toolkit.
Also, take a look at Plato’s great exposition on all things ME; this is a great resource: https://www.win-raid.com/t596f39-Intel-Management-Engine-Drivers-Firmware-amp-System-Tools.html



Post a Comment
Be sure to select an account profile (e.g. Google, OpenID, etc.) before typing your comment!