Related to 800-147 and building upon its foundation is another NIST spec, 800-155.
SP 800-155
DRAFT BIOS Integrity Measurement Guidelines
NIST announces the public comment release of NIST Special Publication 800-155, BIOS Integrity Measurement Guidelines. This document outlines the security components and security guidelines needed to establish a secure Basic Input/Output System (BIOS) integrity measurement and reporting chain. BIOS is a critical security component in systems due to its unique and privileged position within the personal computer (PC) architecture. A malicious or outdated BIOS could allow or be part of a sophisticated, targeted attack on an organization —either a permanent denial of service (if the BIOS is corrupted) or a persistent malware presence (if the BIOS is implanted with malware). The guidelines in this document are intended to facilitate the development of products that can detect problems with the BIOS so that organizations can take appropriate remedial action to prevent or limit harm. The security controls and procedures specified in this document are oriented to desktops and laptops deployed in an enterprise environment.
The public comment period closed on January 20, 2012.
Although still labeled “draft”, I am not aware of any update to 800-155 since its original release and public comment period. I believe the impetus for the creation of 800-155 was:
In September, 2011, a security company discovered the first malware designed to infect the BIOS, called Mebromi. "We believe this is an emerging threat area," said Regenscheid. These developments underscore the importance of detecting changes to the BIOS code and configurations, and why monitoring BIOS integrity is an important element of security.
What is 800-155 About?
Today, enterprise software vendors sell corporate anti-virus products. These products inventory all the PCs in an organization, run anti-virus scans, and report the results to the IT administrator via a centralized management application. The IT administrator can thus manage the network by quarantining infected machines and then cleaning any virus/malware detected.
In a similar fashion, 800-155 lays out guidelines for creating an enterprise software system that communicates with all the PCs on the network, but, rather than scanning for viruses at the OS level, the system compares BIOS measurements to known-good “golden” measurements. If the comparison fails on a particular PC, the system BIOS has been compromised and the IT administrator can take action.
By “measurement”, we’re talking about taking a cryptographic hash of BIOS code or data before it’s run or read. Only if the hash matches its expected value will the system continue with the execute or read operation. This is a big topic, and you’ve perhaps heard of Intel’s Trusted Execution Technology. (TxT) Read the TxT Wikipedia article to get a better idea of what 800-155 means by “measurement”.
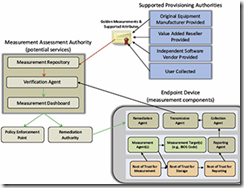
Components of the System
I would summarize the specification by classifying its contents into the following concepts:
- Various Roots of Trust (RoT) are discussed. A RoT is a known-good and inviolable foundation from which the rest of a secure system can be based.
- RoT – Measurement is about providing a cryptographic processor to make reliable integrity measurements
- RoT – Storage is about providing a tamper-proof store of the integrity measurements, in proper sequence.
- RoT – Reporting is transmitting the results of the integrity measurements from the PC to the management application in a secure manner.
- BIOS Boot Code integrity
- The integrity of the BIOS boot block, POST code, ACPI code (among other possibilities) is measured and verified.
- BIOS Data integrity
- The integrity of the BIOS configuration is likewise measured and verified. Example: BIOS Setup options.
- Measurement Authority
- The management application used by the IT administrator to manage the enterprise.
- Communicates with the PCs on the network with hashes and nonces to guarantee accurate and fresh data.
- Golden Measurements
- The management application stores the expected (called “golden”) measurements. These get compared to the measurements sent in over the network from each PC.
- The golden measurements typically would come from the PC OEM (Dell, HP, etc.).
- Remediation
- Quarantining infected systems by removing them to a restricted, locked-down part of the network.
- Fixing the infected system via a BIOS update or reconfiguration.
The appendices go on to propose various options for implementing the roots of trust, and also possible ways the measurement system could be implemented in a real-world enterprise.
Conclusion
I can only give an overview of 800-155 here, and encourage you to read the paper yourself. The paper touches on many, many security technologies, as evidenced by the extensive References section in the back. Examples of prerequisite technologies presumed by 800-155: Trusted Computing and the work of the Trusted Computing Group; digital signatures, SMBIOS, Trusted Platform Modules (TPM), SMM mode… plus more. It’s all interesting reading for any BIOS security developer, and I hope I’ve whetted your appetite for checking out the paper.
Download from NIST here:
http://csrc.nist.gov/publications/drafts/800-155/draft-SP800-155_Dec2011.pdf


Post a Comment
Be sure to select an account profile (e.g. Google, OpenID, etc.) before typing your comment!