
The Mitre team of John Butterworth, Sam Cornwell, Corey Kallenberg, and Xeno Kovah created a tool called Copernicus to test BIOS images for vulnerability to rootkits. From their own executive summary:
Copernicus is a tool to evaluate BIOS security on Intel PCs. A writable BIOS opens a system up to a very stealthy, powerful, and persistent backdoor. It allows the possibility that the attacker can brick the system (make it unbootable) on demand. Unlike attacks on software, this firmware attack cannot be recovered from without physical removal of the BIOS firmware chip.
The Copernicus agent takes two actions to evaluate BIOS vulnerability. First it dumps the contents of the flash chip. Second it checks access control registers that determine whether the BIOS is writable or not. This data can then be analyzed. The BIOS dump can be compared against a known clean copy to check for the presence of implants. The control registers can be be analyzed to determine of the BIOS is writable and therefore vulnerable.
How does it work? The tool is implemented as a kernel driver that creates a file containing the BIOS dump and a file containing the raw configuration information. When deployed in enterprise environments, scripts can send the raw BIOS dump and configuration information to a server for post-processing. This processing can indicate whether a given BIOS differs from an expected baseline.
Running Copernicus
Running the tool is simple, just execute the batch file standalone.bat:
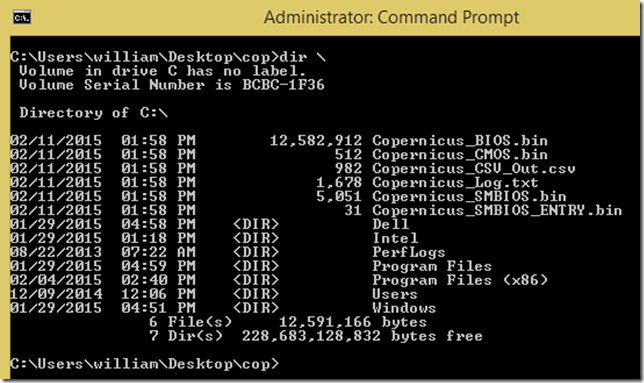
The Copernicus process will take at most thirty seconds depending on the size of your system’s SPI part(s), at which point the output will be left in the root directory of your system’s C: drive:
The files named Copernicus_* are the files generated by the tool. I’ve placed the files from my test run here for reference:
https://github.com/WilliamLeara/BasicInputOutput/tree/master/Copernicus
Copernicus 2
The Copernicus guys wisely realized that a rootkit detection tool is of limited value if there is no way to prove that the results of the test are genuine. After all, the whole point of a rootkit is to intercept low-level commands, change their results, and then send the falsified results to the unsuspecting user. In this way, the rootkit cannot be detected by anti-virus software because the low-level APIs the AV software relies on are already compromised. Since the user doesn’t see anything out of the ordinary, he doesn’t realize there is a problem.
Introducing Copernicus 2: a version of Copernicus that utilizes the system’s Trusted Platform Module (TPM) and Intel’s Trusted Execution Technology (TXT) to verify that the test commands being run and the answers coming back are genuine and tamper-free.
These additional safeguards come at the cost of additional setup steps and prerequisites: namely, 1) an activated TPM, and 2) a system that supports Intel TXT.
My test run was not successful. In Copernicus2_Log.txt I see the message:
Error: Unknown ICH: 0x9cc3.
Error: Unknown MCH: 0x1604.
… and so perhaps this is the root of the problem. I ran the test on a Broadwell-based system—perhaps the hardware is too new for Copernicus 2? Anyway, see my complete test run collateral (with file names Copernicus2*) at:
https://github.com/WilliamLeara/BasicInputOutput/tree/master/Copernicus
Conclusion
The Copernicus tool should be part of the toolkit of any BIOS engineer interested in security. It gives an indication of how easily your system BIOS can be taken over by rootkit malware. It’s free, powerful, and backed by the well-respected folks from Mitre*.
Download the Copernicus binary and documentation:
Copernicus 1:
http://www.mitre.org/sites/default/files/copernicus_pr.zip
Copernicus 2:
http://www.mitre.org/sites/default/files/Xeno_BIOS%20Cop2_Copernicus2_Distributable.zip
Copernicus 2 white paper: http://www.mitre.org/sites/default/files/publications/Copernicus2-SENTER-the-Dragon-CSW-.pdf
*some of the Mitre folks just recently became Legbacore folks. More here.



Post a Comment
Be sure to select an account profile (e.g. Google, OpenID, etc.) before typing your comment!